Setting up SSL locally
Contents
Setting up HTTPS locally can be useful if you're trying to debug hard to replicate issues (e.g cross domain cookies, etc).
There are two ways you can get HTTPS locally:
- ngrok
- NGINX and a local certificate.
The easiest option is to use ngrok.
Set up SSL via ngrok
Sign up for an ngrok account (or sign in with GitHub) and run
ngrok authtoken <TOKEN>Find your ngrok config file location:
On macOS, this will show ~/Library/Application Support/ngrok/ngrok.yml (XDG location). The legacy location ~/.ngrok2/ngrok.yml is deprecated.
- Edit your ngrok config file and add the following after the line with
authtoken: <TOKEN>:
- Start ngrok. This will give you tunnel URLs such as https://68f83839843a.ngrok-free.dev
- Copy the HTTPS URL for the tunnel to port 8234 and set it as the value for the
JS_URLenvironment variable. Then, start webpack:
- Use the same URL as the value for
JS_URLagain and start the Django server
- Open the HTTPS URL for the tunnel to port 8000.
Tips & Tricks
If you're testing the Toolbar, make sure to add the ngrok urls to the list on the 'Project Settings' page.
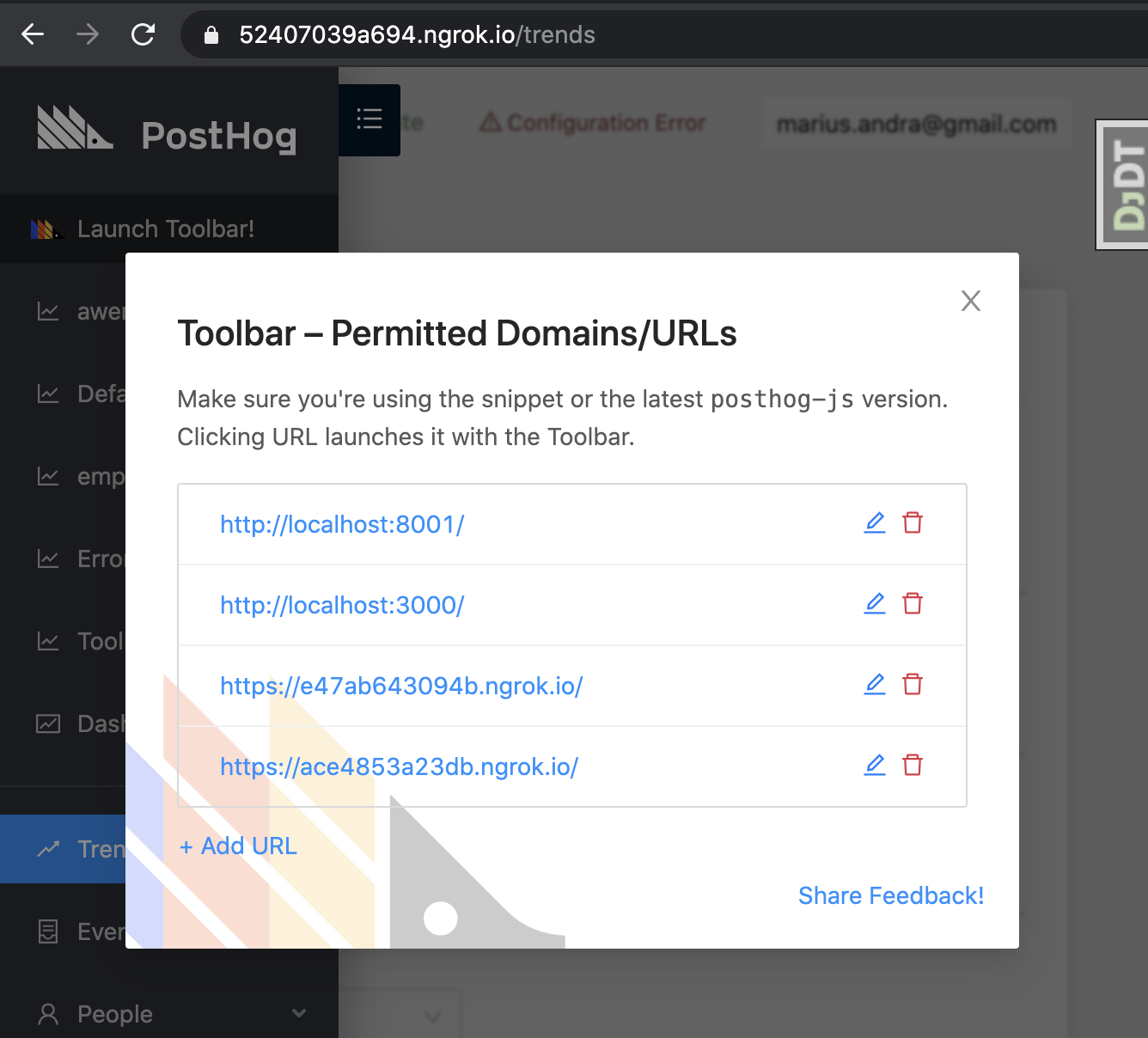
Also, watch out, network requests can be slow through ngrok:
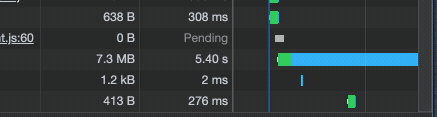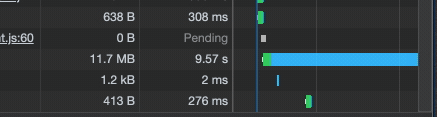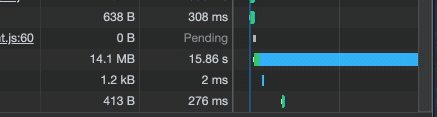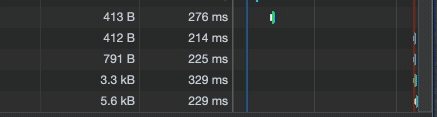
Set up SSL via NGINX and a local certificate
- Update openssl if "openssl version" tells you "LibreSSL" or something like that.
In case brew install openssl and brew link openssl don't work well, use
/usr/local/opt/openssl/bin/openssl instead of openssl in the next step.
- Create key
- Trust the key for Chrome/Safari
- Add
secure.posthog.devto /etc/hosts
- Install nginx (
brew install nginx) and add the following config in/usr/local/etc/nginx/nginx.conf
- Add the following command to start nginx
- You can stop the nginx server with
- To run local development, use








