Identifying users
Contents
Linking events to specific users enables you to build a full picture of how they're using your product across different sessions, devices, and platforms.
This is straightforward to do when capturing backend events, as you associate events to a specific user using a distinct_id, which is a required argument.
However, in the frontend of a web or mobile app, a distinct_id is not a required argument — PostHog's SDKs will generate an anonymous distinct_id for you automatically and you can capture events anonymously, provided you use the appropriate configuration.
To link events to specific users, call identify:
Events captured after calling identify are identified events and this creates a person profile if one doesn't exist already.
Due to the cost of processing them, anonymous events can be up to 4x cheaper than identified events, so it's recommended you only capture identified events when needed.
How identify works
When a user starts browsing your website or app, PostHog automatically assigns them an anonymous ID, which is stored locally.
Provided you've configured persistence to use cookies or localStorage, this enables us to track anonymous users – even across different sessions.
By calling identify with a distinct_id of your choice (usually the user's ID in your database, or their email), you link the anonymous ID and distinct ID together.
Thus, all past and future events made with that anonymous ID are now associated with the distinct ID.
This enables you to do things like associate events with a user from before they log in for the first time, or associate their events across different devices or platforms.
Using identify in the backend
Although you can call identify using our backend SDKs, it is used most in frontends. This is because there is no concept of anonymous sessions in the backend SDKs, so calling identify only updates person profiles.
Best practices when using identify
1. Call identify as soon as you're able to
In your frontend, you should call identify as soon as you're able to.
Typically, this is every time your app loads for the first time, and directly after your users log in.
This ensures that events sent during your users' sessions are correctly associated with them.
You only need to call identify once per session, and you should avoid calling it multiple times unnecessarily.
If you call identify multiple times with the same data without reloading the page in between, PostHog will ignore the subsequent calls.
2. Use unique strings for distinct IDs
If two users have the same distinct ID, their data is merged and they are considered one user in PostHog. Two common ways this can happen are:
- Your logic for generating IDs does not generate sufficiently strong IDs and you can end up with a clash where 2 users have the same ID.
- There's a bug, typo, or mistake in your code leading to most or all users being identified with generic IDs like
null,true, ordistinctId.
PostHog also has built-in protections to stop the most common distinct ID mistakes.
3. Set up person profiles and properties
You'll notice that one of the parameters in the identify method is a properties object.
This enables you to set person properties.
Whenever possible, we recommend passing in all person properties you have available each time you call identify, as this ensures their person profile on PostHog is up to date.
Person properties can also be set being adding a $set property to a event capture call.
See our person properties docs for more details on how to work with them and best practices.
Get the current user's distinct ID
You may find it helpful to get the current user's distinct ID. For example, to check whether you've already called identify for a user or not.
To do this, call the following:
The ID returned is either the ID automatically generated by PostHog or the ID that has been passed by a call to identify().
Reset
If a user logs out on your frontend, you should call reset() to unlink any future events made on that device with that user.
This is important if your users are sharing a computer, as otherwise all of those users are grouped together into a single user due to shared cookies between sessions.
We strongly recommend you call reset on logout even if you don't expect users to share a computer.
You can do that like so:
If you also want to reset the device_id so that the device will be considered a new device in future events, you can pass true as an argument:
Alias: Assigning multiple distinct IDs to the same user
Sometimes, you want to assign multiple distinct IDs to a single user. For example, if a distinct ID which is typically used on the frontend is not available in certain parts of your backend code, you can use alias to connect the frontend distinct ID to one accessible on the backend. This will merge all past and future events into the same user.
In the below example, we assign the user with frontend_id another ID: backend_id. This means that any events submitted using either frontend_id or backend_id will be associated with the same user.
There are two requirements when assigning an alias_id:
- It cannot be associated with more than one
distinct_id. - The
alias_idmust not have been previously used as thedistinct_idargument of anidentify()oralias()call. For example: Assume we previously calledposthog.identify('distinct_id_one'). It is not possible to usedistinct_id_oneas an alias ID:
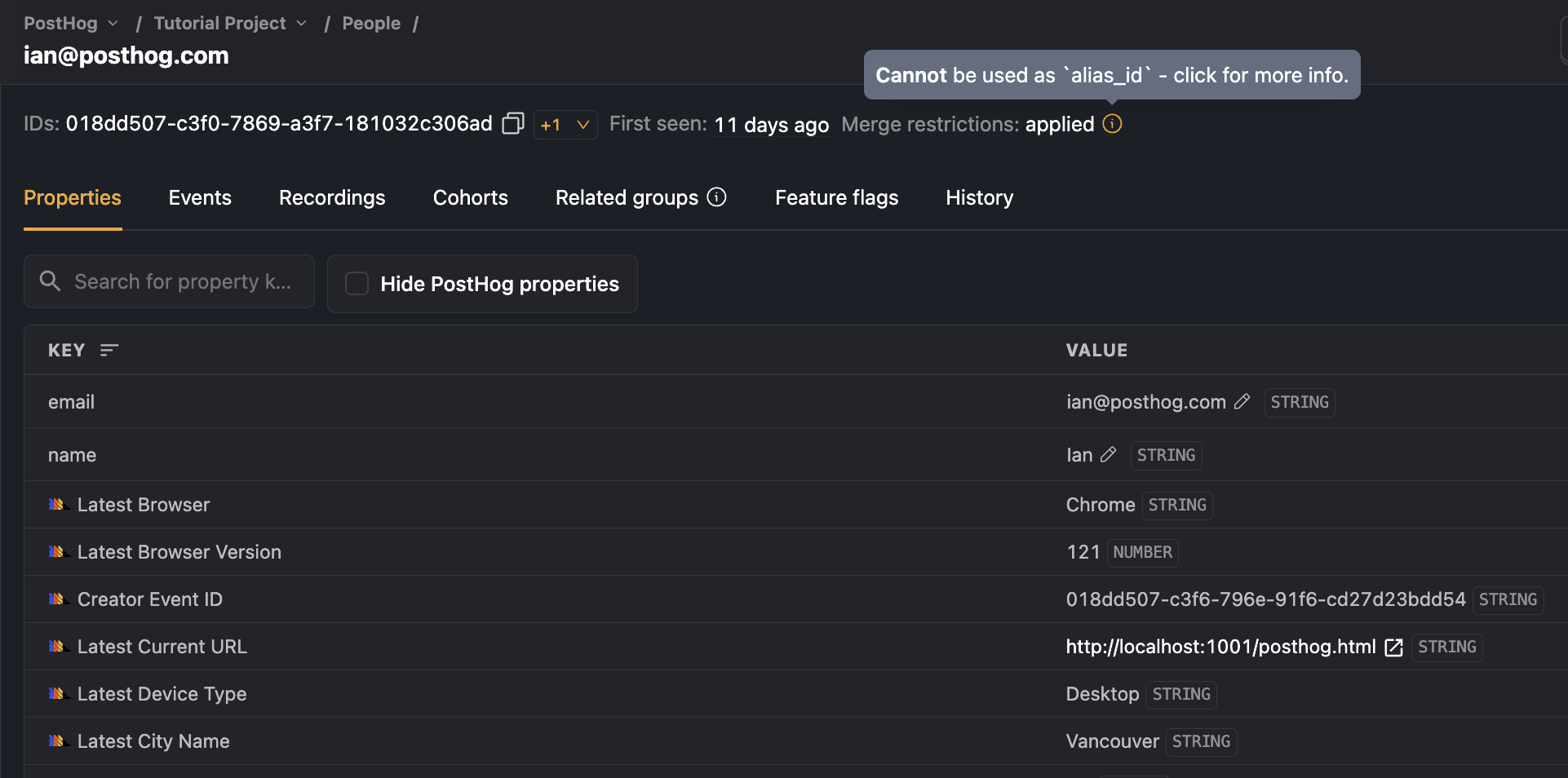
You can view whether a user can be merged into another user using alias when viewing their properties in the PostHog app: Under their ID, you'll see Merge restrictions. This will indicate whether there are merge restrictions or not – i.e., whether you can use their ID as an alias_id or not.
Note: When calling
aliasin the frontend SDKs, if you have set any properties onto the anonymous user, they are merged into the user withdistinct_id. For more details, see the FAQ on how properties are managed when identifying anonymous users.
Troubleshooting and FAQs
What happens if you call identify or alias with invalid inputs?
When calling either of these with invalid inputs (such as in the examples described in this doc e.g., using null strings with identify, or by trying to use a distinct ID of another user as an alias ID), the following will happen:
- We process the event normally (it will be ingested and show up in the UI).
- Merging users will be refused and an ingestion warning will be logged (see ingestion warnings for more details).
- The event will be only be tied to the user associated with
distinct_id.
PostHog also has built-in protections to stop the most common distinct ID mistakes. See the FAQ at the end of this page for more details.
We do not allow identifying users with empty space strings of any length – e.g.,
' ',' ', etc.We do not allow identifying users with the following strings (case insensitive):
anonymousguestdistinctiddistinct_ididnot_authenticatedemailundefinedtruefalse
We do not allow identifying users with the following strings (case sensitive):
[object Object]NaNNonenonenull0
We do not allow identifying a user that has already been identified with a different distinct ID. For example:
How to merge users
It may happen that, due to implementation issues, the same user in your product has multiple users in PostHog associated with them. In these cases, you can use $merge_dangerously to merge multiple PostHog users into a single user.
⚠️ Warnings:
- Merging users with
$merge_dangerouslyis irreversible and has no safeguards! Be careful not to merge users who should not be merged together. Due to the dangers, we don't recommend you merge users frequently, but rather as a one-off for recovering from implementation problems.- Before using
$merge_dangerously, first check if alias would better suit your needs.
Merging users is done by sending a $merge_dangerously event:
How to identify users across platforms
We recommend you call identify as soon as you're able, typically when a user signs up or logs in.
This doesn't work if one or both platforms are unauthenticated. Some examples of such cases are:
- Onboarding and signup flows before authentication.
- Unauthenticated web pages redirecting to authenticated mobile apps.
- Authenticated web apps prompting an app download.
In these cases, you can use a deep link on Android and universal links on iOS to identify users.
- Use
posthog.get_distinct_id()to get the current distinct ID. Even if you cannot call identify because the user is unauthenticated, this will return an anonymous distinct ID generated by PostHog. - Add the distinct ID to the deep link as query parameters, along with other properties like UTM parameters.
- When the user is redirected to the app, parse the deep link and handle the following cases:
- The user is already authenticated on the mobile app. In this case, call
posthog.alias()with the distinct ID from the web. This associates the two distinct IDs as a single person. - The user is unauthenticated. In this case, call
posthog.identify()with the distinct ID from the web. Events will be associated with this distinct ID.
As long as you associate the distinct IDs with posthog.identify() or posthog.alias(), you can track events generated across platforms.
How to split a merged user back into separate users
If you've accidentally linked distinct IDs together that represent different users, or you've made a mistake when merging users, it's possible to split their combined user back into separate users. You can do this in the PostHog app by navigating to the user you'd like split, and then clicking "Split IDs" in the top right corner.
Warning: This will treat the distinct IDs as separate users for future events. However, there is no guarantee as to how past events will be treated – they may be be considered separate users, or be considered a single user for some or all events.
How are properties managed when merging users?
When a User B is merged into another User A, all the properties of the User B are added to User A. If there is a conflict, the properties of User A are prioritized over User B. For example:
How are properties managed when identifying anonymous users?
When an anonymous user is identified as User A, all the properties of the anonymous user are added to User A. If there is a conflict, the properties of User A are prioritized over the anonymous user. For example:








